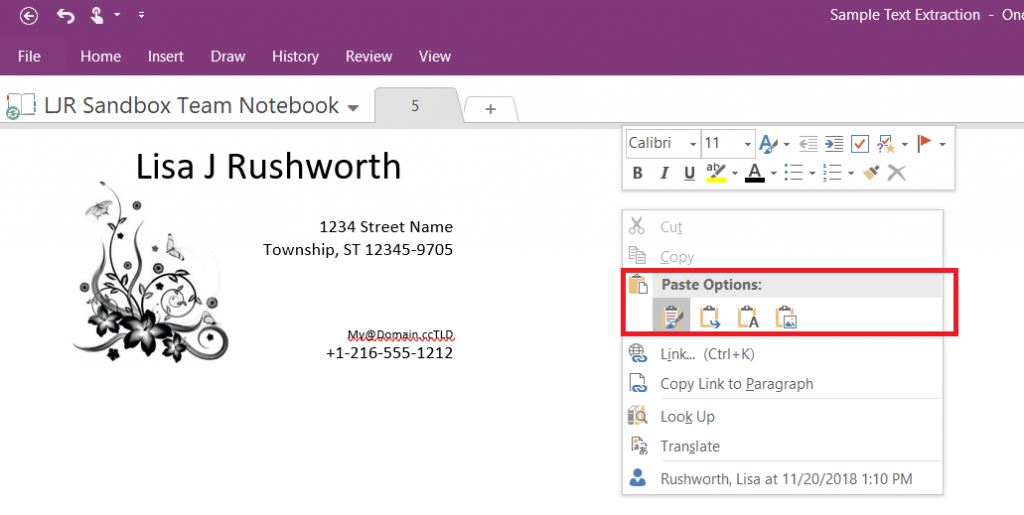
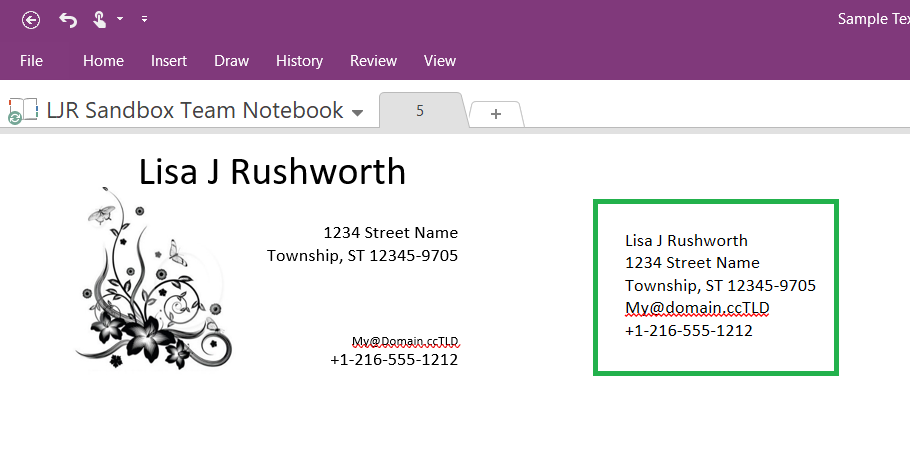
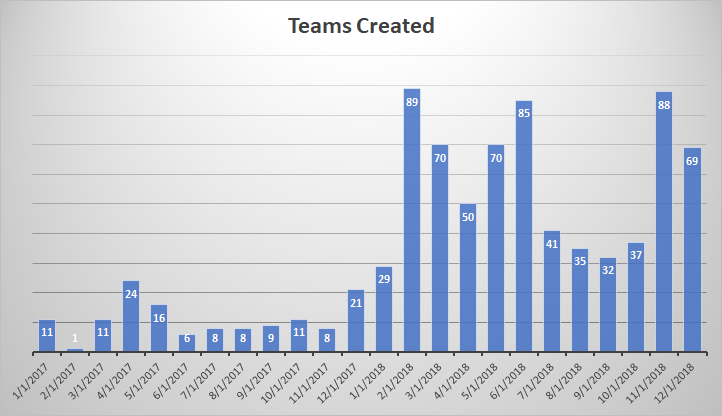
We purchased a house full of Z-wave dimmers (Leviton VRMX-1LZ and DZSM-1LZ) as a Christmas season special from Leviton two years ago. We were really happy to have dimmers throughout the house — we could use the existing lighting as nightlights, have movie nights with a little pathway lighting … and then we installed a few dimmers and realized the bulbs dimmed. But not DIM dimmed. It was a massive bummer, and significantly diminished the couple hundred bucks we’d dropped on these smart dimmers.
We even called Leviton & got a paper they publish with how different bulbs dim with their various dimmers. And realized that all of the bulbs that went down to 1 or 2% were discontinued. Another bummer! The paper is updated periodically, but even the early 2018 iteration failed to yield any in-production well-dimming bulbs.
Over the summer, I came across a review of various dimmable LED light bulbs. The guy had an integrating sphere rigged up and was measuring output and colour — seemed like he put a lot of effort into it (and I’d LOVE to find that write-up again!). His write-up indicated that Home Depot’s “house brand” bulbs, EcoSmart, dimmed down to basically nothing. I added EcoSmart 60W bulbs to my “next time you’re at Home Depot” list and finally remembered to pick them up in September. Except there were two types — plastic ones and glass ones that can be used in closed fixtures. The plastic ones dimmed well — way better than any of the Cree, Phillips, or Lighting Science bulbs we’d tried. But the glass ones — they dimmed to the point of being off. We had to go through and change what the dimmers consider zero because these bulbs were TOO dim. And they didn’t hum, buzz, or flicker. I was thrilled — swapped out the downstairs hallway bulbs with these glass EcoSmart LEDs and the light fixtures have become nightlights.
I wanted to get bulbs for the other hallway, bedrooms, and bathrooms. So I ordered the bulbs online & they showed up. Replaced one set of bedroom bulbs, dimmed them … and they’re about on par with the Cree bulbs we had. Huh? Upon investigation, while the bulbs we got delivered had the exact same part number, they had a different UPC. And a different product code above the UPC. Even odder — the energy draw and estimated annual cost were different. Apparently there are different revisions of the bulbs, and the 02 revision doesn’t dim any better than every other bulb out there.
We returned the bulbs and checked the light bulb aisle at the store for any with UPC 693690563636 and product code ABA19A60WESD01 — and found a bunch on the shelves. They also had the 02 revision and a 03 revision. Since the 01 ones were a known quantity, we bought them. And they dim down to nothing! It’s been just about two years, but the dimmers we’ve put in are finally PERFECT.