Microsoft uses the number of 100-nanosecond intervals since 01 January 1601. Why? No idea. But I’ve had to deal with their funky large integer for a DateTime value as long as I’ve been working with AD. I’ve written functions to turn it int something useful, but that’s a lot of effort when I see a lockoutTime and need to know how recent that is. Enter w32tm which has an “ntte” switch — this allows me to readily tell that the lockout was at 3:01 today and something I need to be investigating.
Category: System Administration
Blocking Device Internet Access
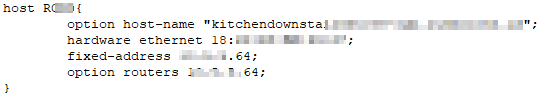
We block Internet access for a lot of our smart devices. All of our control is done through the local server; and, short of updating firmware, the devices have no need to be chatting with the Internet. Unfortunately, our DSL modem/router does not have any sort of parental control, blocking, or filtering features. Fortunately, ISC DHCPD allows you to define per-host options. Setting the router to the device’s IP (0.0.0.0 may work as well) allows us to have devices that can communicate with anything on their subnet without allowing access out to other subnets or the Internet.
Viewing and recording packets using tshark
This time, I’m writing this down so I don’t have to keep looking it up. To display some packet info to the screen while writing a network capture to a file, include the -P option (older versions of tshark used -S)
2021-04-18 13:58:58 [lisa@server ~]# tshark -f "udp port 123" -w /tmp/ntpd.cap -P Running as user "root" and group "root". This could be dangerous. Capturing on 'enp0s25' 1 0.000000000 10.x.x.x → x.x.x.18 NTP 90 NTP Version 4, client 2 3.898916081 10.x.x.x → x.x.x.199 NTP 90 NTP Version 4, client 3 7.898948128 10.x.x.x → x.x.x.20 NTP 90 NTP Version 4, client 4 7.928749596 x.x.x.20 → 10.x.x.x NTP 90 NTP Version 4, server 5 9.898958577 10.x.x.x → x.x.x.76 NTP 90 NTP Version 4, client 6 9.949450324 x.x.x.76 → 10.x.x.x NTP 90 NTP Version 4, server 7 10.898981132 10.x.x.x → x.x.x.185 NTP 90 NTP Version 4, client 8 11.009163093 x.x.x.185 → 10.x.x.x NTP 90 NTP Version 4, server
Finding current leases in ISC DHCPD
A quick grep statement to find stanzas for leases issued the current day:
TODAY=`printf ‘%(%Y/%m/%d)T’ -1`; egrep -A9 -B1 “starts . $TODAY” /var/lib/dhcpd/dhcpd.leases;unset TODAY
Console access from virsh
I had a whole host of problems that were eventually resolved by rebooting the physical server … but, in the process of trying to figure out exactly what was wrong, I wanted to console into the virtual machines from the physical server. Using “virsh console vmname” should have worked … but it didn’t. Turns out you’ve got to enable a service on each guest before you’re able to console in from the physical server. To do so, run:
systemctl enable serial-getty@ttyS0.service
And, if you want to connect in *right now*, also start the service:
systemctl start serial-getty@ttyS0.service
Now, running “virsh console vmname” doesn’t appear to do much … but, if you hit the enter key, you’ll get a logon prompt for the VM.
Linux: Identifying Large Packages
The disk filled up on our primary server, and there wasn’t anything obvious like a decade worth of log files to clean up. I had to resort to uninstalling ‘stuff’ (it was, after all, installing ‘stuff’ that created the problem … tons of X11-related stuff for troubleshooting purposes). There is a way to list installed packages by size:
rpm -qia|awk '$1=="Name" { n=$3} $1=="Size" {s=$3} $1=="Description" {print s " " n }' |sort -n
MTU Probing
We’ve had a number of very strange network problems lately — Zoneminder cannot talk to cameras, clients veg out talking to Myth, Twonky is non-functional (even the web page — you get enough of the header to have a title, but the page just hangs, Scott cannot get to our Discourse site. And, more frustratingly, he cannot SSH to some of our hosts. Using “ssh -v” and throwing on a bunch of flags to not attempt key auth (-o PasswordAuthentication=yes -o PreferredAuthentications=keyboard-interactive,password -o PubkeyAuthentication=no) and his connection still hung. But, at least, I could see something. The last thing the SSH connection reported is:
debug1: expecting SSH2_MSG_KEX_ECDH_REPLY
Which I’ve seen before … fortunately when I had a great Unix support guy working in the same office building that I did. Who let me stop over and bounce really oddball problems off of him. He told me to enable mtu probing.
echo 1 >/proc/sys/net/ipv4/tcp_mtu_probing
And, if that doesn’t work, use “echo 2”. Which …. yeah, wouldn’t have been any of my first thirty guesses. Cloudflare published a good article on what exactly MTU path discovery is, and I can RTFM enough to figure out what I’ve set here. But no idea what’s got a smaller MTU than our computers.
tcp_mtu_probing - INTEGER
Controls TCP Packetization-Layer Path MTU Discovery.
0 - Disabled
1 - Disabled by default, enabled when an ICMP black hole detected
2 - Always enabled, use initial MSS of tcp_base_mss.Windows: Network Location Awareness Service
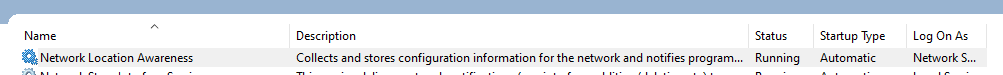
Every once in a while, my Windows server says it has no Internet connection. It does. It can even use the connection. But the little systray icon has a yellow glif and it says there’s no connection. It’s cosmetic, but annoying. I’ve discovered, however, that there’s a “Network Location Awareness” service that can be restarted to re-evaluate the connectivity status.
PIP SSL Error
Upgraded pip today, and I pretty quickly regretted it. SSL Error attempting to install anything from the Internet (and, amazingly, some things where I downloaded the wheel file). The answer is to downgrade PIP until you hit a version that doesn’t have the error. Annoying. Not sure what the latest rev I could have used was — going back one level and getting the error in loop was more time than I could devote to the project, so I just jumped back six months. Had success with 20.0.2 and left working alone.
Everything from 20.3.1 through 21.0.1 has this failure:
D:\tmp\5\pip>pip install basic_sftp
WARNING: Retrying (Retry(total=4, connect=None, read=None, redirect=None, status=None)) after connection broken by ‘SSLError(SSLError(1, ‘[SSL: WRONG_VERSION_NUMBER] wrong version number (_ssl.c:1076)’))’: /simple/basic-sftp/
WARNING: Retrying (Retry(total=3, connect=None, read=None, redirect=None, status=None)) after connection broken by ‘SSLError(SSLError(1, ‘[SSL: WRONG_VERSION_NUMBER] wrong version number (_ssl.c:1076)’))’: /simple/basic-sftp/
WARNING: You are using pip version 20.3.1; however, version 21.0.1 is available.
You should consider upgrading via the ‘c:\programs\anaconda3\python.exe -m pip install –upgrade pip’ command.
SCP From Solaris to RHEL?
Evidently you cannot just scp files from an old Solaris box when you’re on a RHEL/CentOS system … there’s an incompatibility between them that requires you to (1) install scp1 on the Solaris server {not likely in a prod environment} or (2) use sftp to transfer the files.
Server1: Red Hat Enterprise Linux Server release 7.6 (Maipo)
Server2: Solaris 5.9
lisa@server1:~/$ scp lisa@server2:/data/stuff/file1.txt ./input/
lisa@server2’s password:
scp: warning: Executing scp1.
scp: FATAL: Executing ssh1 in compatibility mode failed (Check that scp1 is in your PATH).