Coupling the recent revelations about Trump Jr’s meetings and The New Republic’s article on Russian mafia money being laundered through Trump properties … collusion may be the more flattering story of the events. The alternative is a broke businessman so desperate for a buck that he doesn’t care where the money comes from who essentially becomes the Russian mafia’s go-to patsy for laundering their money. A rube whose incredible ego led him to run for president. At which point the Russians realize they’ve got a stooge in the hand and unilaterally undertake to support his campaign.
Month: July 2017
Creating a Docker Image
There are a lot of pre-built images available on Docker Hub — most recent OS builds, Apache, MariaDB, there’s even an Oracle Enterprise database server. If you’ve got a fairly recent OS, you can start from that base image and use Dockerfile (or in a CI/CD pipeline, the before_script) to install additional components. But if your OS is out-of-date … you still need a test platform that matches production! You can create your own Docker image without using a base.
First, you need a server. This can be your current dev box (or your current prod box, but I avoid touching the prod boxes!). It can be a new install. Either way, you need a server. Log in and su to root. Then tar off the installation:
tar -czf /image/centos51.tgz ./ --exclude /image
Once you’ve got a tar of the server, scp the tar to whatever computer is running your docker client. Import the image to Docker. (You can tag the image and upload it to a registry, if you’ve got one.)
docker load centos51.tgz sampleproject/cent51
Finally, start a container based on the image:
docker run -p 80:80 -p 443:443 -v /data/docker/certs:/etc/httpd/certs -v /data/docker/conf.d/SampleProjectSite.conf:/etc/httpd/conf.d/SampleProjectSite.conf -v /data/git/SampleProjectCode:/var/www/vhtml/SampleProject/html -dit --name SampleProject sampleproject/cent51 /bin/bash
Free Speech
As the “defense of the day” goes, free speech is about the worst claim to make when accused of colluding with a foreign government to undermine an American election. Not to lead a parade of horribles, but if accepting stolen information on a political opponent is free speech … why wouldn’t accepting IP garnered through industrial espionage equally protected?
If you go for crazy extrapolation — Citizens United tells me that spending money is ‘speech’, so I should be able to buy a Rolex and laptop from the back of some dodgy van downtown. Free speech, ya know.
Butterflies!
Making Soap Molds – Material Research
Before trying to print my own soap molds, I need to identify what characteristics I like in a mold. I find flexible molds easier to work with than rigid ones – I’ve snapped a number of molds trying to remove the soap.
So I am trying to find a material that will withstand heat generated by saponification. It looks like saponification can yield temperatures up to 88° C. I don’t want to buy pounds of different filaments to test them out, but GlobalFSD offers “sample” size filament cuttings that are perfect for experimentation or small niche products (e.g. printing glow in the dark mailbox numbers).
One material included information about temps for printed objects, so I’ve contacted the other manufacturers to see if they provide any sort of guidance.
| Material | Max C | Min C | Notes | URL |
| NinjaFlex | 65.5 | -30 | https://www.globalfsdusa.com/ninjaflex-by-fenner-drives.html?category_id=20 | |
| CrystalFlex | – | – | Food safe | https://www.globalfsdusa.com/crystalflex-tm-by-formfutura.html?category_id=20 |
| FilaFlex | https://www.globalfsdusa.com/filaflex-by-recreus-1-75mm.html?category_id=20 | |||
| FlexFill | 230 | -40 | https://www.globalfsdusa.com/flexfil-98a-by-fillamentum-1-75mm.html?category_id=20 | |
| F41 Flex | 75 | -20 | https://www.globalfsdusa.com/f41-flex-tm-1-75mm-black-polyolefin-filament-by-forefront.html?category_id=20 |
That’s what we do in business
The most telling phrase from Trump Jr’s interview with Hannity last night — “That’s what we do in business”. He continued to explain that they take whatever information is out there and then decide how to use it. Illegally garnered information about a politician that can be used to influence the decision process to TrumpCo’s advantage? He may love it, but it’s also called blackmail. And is illegal. A competitor’s business plans or IP gathered through corporate espionage? Hiring former employees of competitors for their inside knowledge or sales leads? I’m not saying I doubt that is how Trump does business, but it hardly paints a flattering picture of the organisation. And I hope that a head of the company broadcasting the company’s willingness to use illegally gathered information to the detriment of their competitors is sufficient to bring an investigation into the company’s operations as well.
Part of our support
There’s a sentence in Trump Jr’s released e-mail messages that really stands out to me: “This is obviously very high level and sensitive information but is part of Russia and its government’s support for Mr. Trump”
For a group of people who have spent almost a year now denying that Russia or its government in any way supported, promoted, aided, or favored Trump … passing around an e-mail thread about something that is part of Russia and its government’s support seems ironic. But extra super odd is that no one — neither Trump Jr, nor the people to whom he forwarded the message — found the phrase worthy of remark. Like they already know about Russia and its government providing support for Trump. More like “this message is part of that ongoing situation we all know about” rather than “this message is part of some new and surprising endeavor”.
Furls Crochet Along
Furls makes some beautiful crochet hooks — I picked some up a few years ago in a holiday promo coding failure (free shipping != 50$ off the order) and have been on their newsletter ever since. They’ve got a lot of cool project ideas – a lot of amigurumi critters and crochet along projects. I keep most of them, but nothing has been so awesome that I just had to do it. Until today.
This month’s crochet along project is a sun hat! I am really looking forward to making my own hat. I ordered the materials already – hopefully they’ll get here within a week so I can actually crochet along with the project.
Alternative Fact: Intentions Do Not Matter
Alternative Fact: Kelly Ann Conway, in reference to Trump Jr scheduling a meeting with a Russian lawyer who promised damaging info on Clinton but was actually just tricked into scheduling a meeting to discuss adoptions: “Let’s focus on what did not happen in that meeting. No information provided that was meaningful. No action taken. Nothing”
Real fact: I think anyone who has contacted law enforcement officers when trying to put out a hit or got caught up in a solicitation sting can tell you … what you intended to do can be criminal even if your attempt is thwarted. It may be mitigating if he did not know who was offering damaging information about a political opponent. But in the middle of the DNC being hacked and information from the hacks being released (and the candidate specifically requesting the hackers find the deleted e-mail messages), wouldn’t you be suspicious of someone offering up damaging details about the opposition??
Kerberos Authentication on Tomcat
I finally got around to testing out TomCat 8 and setting up Kerberos authentication for a “single sign-on” experience (i.e. it re-uses the domain logon Kerberos token to authenticate users). This was all done in a docker image, so the config files can be stashed and re-used by anyone with Docker.
First you need an account – on the account properties page, the DES encryption needs to be unchecked and the two AES ones need to be checked. The account then needs to have a service principal name mapped to it. That name will be based on the URL used to access the site. In my case, my site is http://lisa.example.com:8080 (SPNs don’t mind http/https or port numbers) so my SPN is HTTP/lisa.example.com … to set the SPN, run
setspn -A HTTP/lisa.example.com sAMAccountNameOfMyNewlyCreatedAccount
Then generate the keytab:
ktpass /out .\lisa.example.com.keytab /mapuser sAMAccountNameOfMyNewlyCreatedAccount@EXAMPLE.COM /princ HTTP/lisa.rushworth.us@EXAMPLE.COM /pass P@ssw0rdG03sH3r3
** Note about keytabs – there is a KVNO (key version number) associated with a keytab file. When security-related attributes on the account are changed, the KVNO is incremented. Aaaand you need a new keytab. This means you need to be able to get a new keytab if you plan on changing the account password, but it also means that tweaking account settings can render your keytab useless. Get the account all sorted (check off password never expires if that’s what you want, check off user cannot change password, etc) and then generate the keytab.
While you’re working on getting the SPN and keytab stuff sorted, get docker installed and running on your box. I use Docker CE (free) on my Windows laptop, and I’ve had to disable the firewall to allow access from external clients. I would expect a rule (esp one allowing anything to make an inbound connection to 8080/tcp!) would sort it, but I’ve always had the port show as filtered until the firewall is turned off. YMMV.
I create a folder for files mapped into docker containers (i.e. c:\docker) and sub-folders for each specific container. All of the files from TomcatKerberosConfigFiles are unzipped into that folder. The test website is named lisa.rushworth.us and is either set up in DNS or added to c:\windows\system32\drivers\etc\hosts on the client(s) that will access the site. And, of course, there’s a client machine somewhere logged onto the domain. You are going to need to tweak my config files for your domain.
In jaas.conf — I have debug on. Good for testing and playing around, bad for production use. Also you’ll need your SPN and keytab file name
principal="HTTP/lisa.example.com@EXAMPLE.COM" keyTab="/usr/local/tomcat/conf/lisa.example.com.keytab"
In krb5.conf — the encryption is about the only thing you can keep. Use your hostnames and domain name (REALM). If you have multiple domain controllers, you can have more than one “kdc = ” line in the realms.
[libdefaults]
default_realm = EXAMPLE.COM
default_keytab_name = /usr/local/tomcat/conf/lisa.rushworth.us.keytab
default_tkt_enctypes = aes128-cts rc4-hmac des3-cbc-sha1 des-cbc-md5 des-cbc-crc
default_tgs_enctypes = aes128-cts rc4-hmac des3-cbc-sha1 des-cbc-md5 des-cbc-crc
permitted_enctypes = aes128-cts rc4-hmac des3-cbc-sha1 des-cbc-md5 des-cbc-crc
forwardable=true
[realms]
RUSHWORTH.US = {
kdc = exchange01.example.com:88
master_kdc = exchange01.example.com:88
admin_server = exchange01.example.com:88
}
[domain_realm]
example.com= EXAMPLE.COM
.example.com= EXAMPLE.COM
In web.xml – Roles may need to be sorted around (I’m not much of a TomCat person, LMGTFY if you want to do something with roles). Either way, the realm needs to be changed to yours
<realm-name>EXAMPLE.COM</realm-name>
Once Docker is running and the files are updated with your domain info, install the tomcat:8.0 image from the default repository. Start the container mapping all of the custom config files where they go:
docker run -detach --publish 8080:8080 --name tomcat8 --restart always -v /c/docker/tomcat8/tomcat-users.xml:/usr/local/tomcat/conf/tomcat-users.xml:ro -v /c/docker/tomcat8/lisa.example.com.keytab:/usr/local/tomcat/conf/lisa.example.com.keytab:ro -v /c/docker/tomcat8/krb5.conf:/usr/local/tomcat/conf/krb5.conf:ro -v /c/docker/tomcat8/jaas.conf:/usr/local/tomcat/conf/jaas.conf:ro -v /c/docker/tomcat8/web.xml:/usr/local/tomcat/webapps/examples/WEB-INF/web.xml:ro -v /c/docker/tomcat8/context.xml:/usr/local/tomcat/webapps/examples/WEB-INF/context.xml:ro -v /c/docker/tomcat8/logging.properties:/usr/local/tomcat/conf/logging.properties:ro -v /c/docker/tomcat8/spnego-r9.jar:/usr/local/tomcat/lib/spnego-r9.jar:ro -v /c/docker/tomcat8/login.conf:/usr/local/tomcat/conf/login.conf:ro -v /c/docker/tomcat8/testAuth.jsp:/usr/local/tomcat/webapps/examples/testAuth.jsp:ro tomcat:8.0
A couple of useful things about Docker — the container ID is useful
C:\docker\tomcat8>docker ps CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES 4e06b32e1ca8 tomcat:8.0 "catalina.sh run" 12 minutes ago Up 12 minutes 0.0.0.0:8080->8080/tcp, 0.0.0.0:8888->8080/tcp tomcat8
But most commands seem to let you use the ‘friendly’ name you ascribed to the container. Running “docker inspect” will give you details about the container – including its IP address. I’ve found different images use different settings: some map to localhost on my box, some get an IP address within my DHCP range.
C:\docker\tomcat>docker inspect tomcat8 | grep IPAddress "SecondaryIPAddresses": null, "IPAddress": "172.17.0.2", "IPAddress": "172.17.0.2",
Since this is an image that maps to localhost on my box, I need the lisa.example.com hostname to resolve to my laptop’s IP address. For simplicity, I did this by editing the c:\windows\system32\drivers\etc\hosts file.
Shell into the container:
docker exec -it tomcat8 bash
Update your packages and install the kerberos client utilities:
root@4e06b32e1ca8:/usr/local/tomcat/conf# apt-get update root@4e06b32e1ca8:/usr/local/tomcat/conf# apt-get install krb5-user
Then test that your keytab is working:
root@4e06b32e1ca8:/usr/local/tomcat/conf# kinit -k -t ./lisa.example.com.keytab HTTP/lisa.example.com@EXAMPLE.COM root@4e06b32e1ca8:/usr/local/tomcat/conf# klist Ticket cache: FILE:/tmp/krb5cc_0 Default principal: HTTP/lisa.example.com@EXAMPLE.COM Valid starting Expires Service principal 07/08/2017 18:27:38 07/09/2017 04:27:38 krbtgt/EXAMPLE.COM@EXAMPLE.COM renew until 07/09/2017 18:27:38
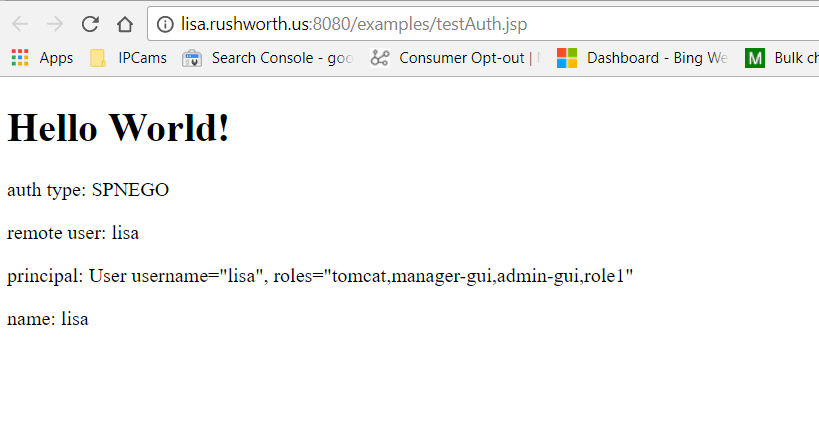
Assuming you don’t get errors authenticating using the Kerberos client utilities, try accessing the TomCat site. I’ve added a testAuth.jsp file to the examples webapp – it shows the logon method, user name, and what roles they have:
- Log files are in /usr/local/tomcat/logs
- If you aren’t using Integrated Authentication for other stuff, you may need to configure your browser to pass along your Kerberos token.
- If you are getting an error in your Catalina log that says:
09-Jul-2017 15:42:55.734 FINE [http-apr-8080-exec-1] org.apache.catalina.authenticator.SpnegoAuthenticator.authenticate Unable to login as the service principal java.security.PrivilegedActionException: GSSException: Defective token detected (Mechanism level: GSSHeader did not find the right tag)
Verify that your SPN is set to the same name being used to access the site. I’m not sure why the configured service principal name doesn’t supersede the user-entered hostname. But I got nothing but auth failures until I actually entered the hostname into my hosts file and used an address that matches the service principal name.