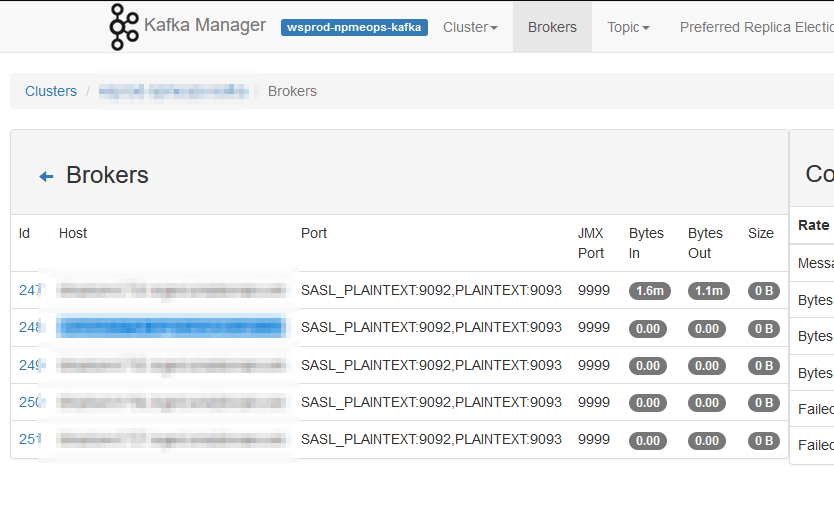
A few months ago, I had dug into a mystery at work — even though JMX was configured to use port 9999, port 9999 was open from the client to the server, and the client was configured to use port 9999 … our Kafka manager tool could only report statistics from the local Kafka server. It failed to retrieve data for the remote ones — saying it was unable to connect. Long story short, JMX uses “it’s” port and two other randomly selected (and not readily configurable) ports. To automate getting JMX working when Kafka is restarted, I built this shell script. It identifies which ports are in use by Java, and it transiently adds them to the firewall rules (since the ports change on each service start, transient firewall rules made sense here). My plan is to link the script to the Kafka unit file as an ExecStartPost directive.
# Get ports linked to java
mapfile -t array_of_ports < <( ss -6 -l -t -p -n | grep java | cut -d ":" -f 4 | grep -v "10.166" | sed -e 's/\ *$//g')
declare -p array_of_ports
for i in "${array_of_ports[@]}"
do
:
if (( i > 20000 )); then
echo "/bin/firewall-cmd --zone=public --add-port=$i/tcp"
output=`/bin/firewall-cmd --zone=public --add-port=$i/tcp`
echo $output
fi
done
mapfile -t array_of_ports < <( ss -4 -l -t -p -n | grep java | cut -d ":" -f 2 | cut -d " " -f 1 | sed -e 's/\ *$//g')
declare -p array_of_ports
for i in "${array_of_ports[@]}"
do
:
if (( i > 20000 )); then
echo "/bin/firewall-cmd --zone=public --add-port=$i/tcp"
output=`/bin/firewall-cmd --zone=public --add-port=$i/tcp`
echo $output
fi
done